KEYSCAN ACCESS CONTROL UNIT
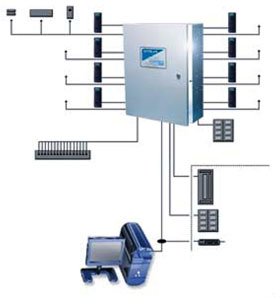
Videocom installs Keyscan and Keri Access Systems that can control from 1 door to thousands of doors. They support combinations of readers and keypads. These systems can store up to 32,000 cards per site with no limit on the number of sites. Retains last 6,000 transactions in activity buffer.
Create up to 511 door groups and 511 door elevator groups create up to 256 time zones, 512 different schedules and 3 different holiday types Monitors door forced open and door held open alarm conditions at reader-controlled doors.
Videocom talented and dedicated sales staff and technician team are genuinely interested in helping you understand and solve your access control security needs. Our friendly staff is ready to assist you and solve your most demanding needs. Just give us a call to see what we mean by friendly and professional staff.
KERI SYSTEMS ACCESS CONTROL UNIT
Today's business has become increasingly IT-centric and Videocom is ready to provide you with the latest access control system to safeguard your facility.

Sophisticated embedded Ethernet-based access control with Doors familiarity and true peer-to-peer IP communication. 50,000 card holders per controller, thousands of doors per system; client/server security with the convenience of a browser; NXT- 4 wire readers are fully supervised with encrypted data between cards/readers; utilize existing networks or pull dedicated CAT 5 cabling.
Doors NetXtreme™, by Keri Systems begins with sophisticated SQL compliant software, operating in a true client/server environment. Feel free to enjoy multiple concurrent users, login across multiple concurrent sites, all accomplished without the imposition of third-party royalty fees. By all accounts, client/server applications have been deemed far superior to browser-based applications for security and information integrity. Still, you can count on Doors NetXtreme™ for ease of use and administration, as the user interface has been designed around an extremely intuitive front-end. Whether your application calls for dozens of operators or thousands of doors, Keri's Doors NetXtreme™ is the answer. Either of our two-door or four-door panels will handle 50K cardholders in resident memory. They can communicate seamlessly over your network or you may decide to create a new network utilizing simple CAT-5 cable. NXT-4D and NXT-2D panels are equipped with 4-pin block and RJ terminals for ease of connection. Once connected, an intuitive, one-button, auto-configuration process with embedded MAC address makes your setup a cinch.






